Your weakest link may be one of your suppliers
The Pain Point:
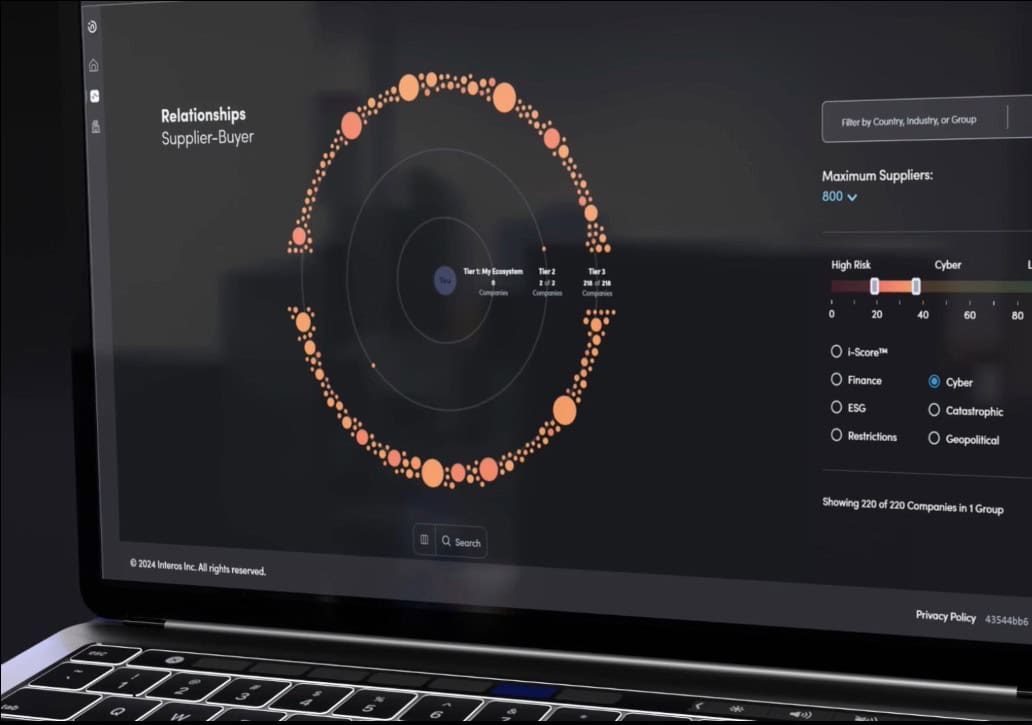
Are My Suppliers Making Me Vulnerable?
Supply chain risk is a major cybersecurity concern, as attackers can exploit vulnerabilities in third-party vendors to access networks. Many organizations lack visibility into their suppliers’ security practices, leaving them exposed to threats beyond their control.
The Remedy:
Supplier Risk Can Be Assessed
Our decades of experience working with elite security-conscious organizations has deeply informed our advanced protection strategies. Our battle-tested techniques, blended with our next gen AI/ML innovations, equals a remedy for what you need the most: peace of mind.